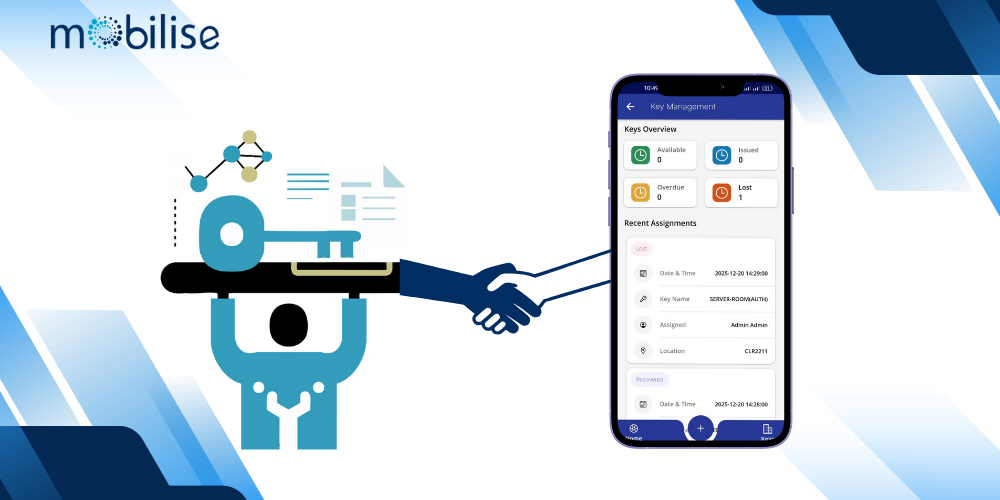
A Key Management System protects sensitive data by securely managing cryptographic keys. These keys support encryption, access control, and secure communication.
The system manages keys across their full lifecycle. It covers key creation, storage, usage, rotation, and retirement. This approach reduces security risks and supports compliance.
As organizations adopt cloud platforms, APIs, and distributed systems, strong key management becomes critical. Tools like OpsSuite by Mobilise help centralize key control and improve security visibility without adding complexity.
What Is a Key Management System (KMS)
A Key Management System (KMS) securely creates, stores, and controls cryptographic keys. These keys protect sensitive data and digital communications.
A KMS centralizes the entire key lifecycle. It manages keys from generation to secure deletion.
Organizations use a KMS to control access and rotate keys automatically. It also tracks key usage to prevent unauthorized access.
By centralizing key operations, a KMS simplifies security management. It also supports compliance across cloud, on-premises, and hybrid environments.
Key Management Lifecycle Overview
The key management lifecycle defines how organizations handle cryptographic keys from creation to deletion. Each stage protects data, prevents unauthorized access, and supports compliance.
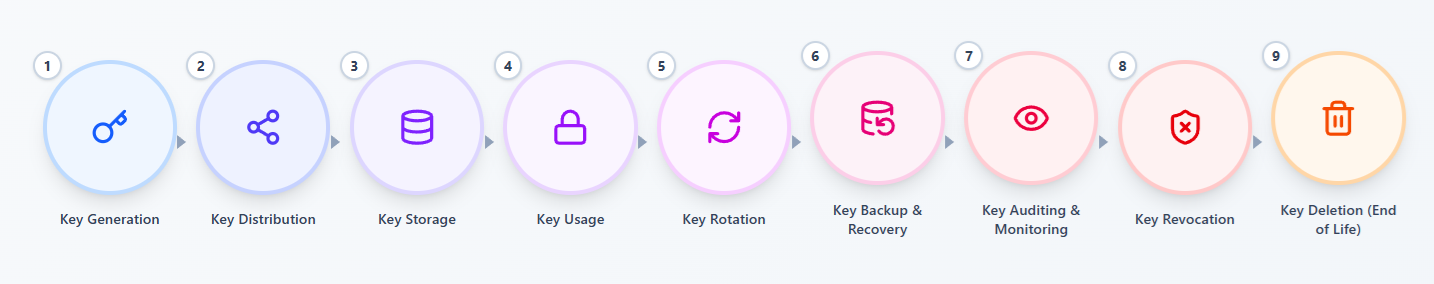
Key Generation
Key generation creates strong cryptographic keys using secure algorithms. Secure generation prevents weak or predictable keys.
Key Storage
Key storage keeps cryptographic keys in a protected environment. Secure storage prevents unauthorized access and key exposure.
Key Distribution
Key distribution delivers cryptographic keys to authorized users and systems only. Secure channels protect keys during transfer.
Key Usage and Access Control
Key usage defines how systems use cryptographic keys. Access control limits usage to approved users and applications.
Key Rotation
Key rotation replaces old keys with new ones at scheduled intervals. Regular rotation reduces the impact of key compromise.
Key Revocation
Key revocation disables compromised or untrusted keys immediately. This step prevents further misuse.
Key Backup and Recovery
Key backup creates secure copies of cryptographic keys. Recovery restores keys without weakening security.
Key Auditing and Monitoring
Key auditing tracks key usage and access events. Monitoring helps detect misuse and supports compliance.
Key Expiration and Decommissioning
Key expiration defines how long a key remains valid. Decommissioning removes expired keys from active systems.
Key Deletion (End of Life)
Key deletion permanently removes cryptographic keys at the end of their lifecycle. Secure deletion prevents recovery or reuse.
Common Key Management Challenges
Organizations often face several challenges while managing cryptographic keys. These issues increase security risks, create compliance gaps, and reduce operational visibility if teams do not address them properly.
| Challenge | Description |
|---|---|
| Lack of Centralized Management | Teams store keys across multiple systems, which reduces visibility and control. |
| Weak Key Storage | Insecure storage exposes cryptographic keys to unauthorized access. |
| Poor Access Control | Excessive permissions allow unauthorized users or systems to use keys. |
| Manual Key Rotation | Manual processes delay key rotation and increase human error. |
| Inadequate Key Monitoring | Limited monitoring prevents early detection of key misuse. |
| Key Loss or Accidental Deletion | Missing backups make it difficult to recover critical keys. |
| Compliance Challenges | Poor key handling leads to audit failures and regulatory issues. |
| Complex Multi-Cloud Environments | Managing keys across cloud and on-prem systems increases complexity. |
| Delayed Key Revocation | Slow revocation allows compromised keys to remain active. |
Importance of Key Management in Cybersecurity
Key management plays a vital role in cybersecurity by protecting the cryptographic keys that secure sensitive data and digital communications. Strong key management prevents unauthorized access and reduces the risk of data breaches.
A well-implemented key management approach supports encryption, access control, and secure authentication across systems. It also helps organizations meet compliance requirements, maintain visibility, and respond quickly to security incidents in cloud, on-premises, and hybrid environments.
Conclusion
Effective key management is essential for protecting sensitive data and maintaining strong cybersecurity practices. By managing cryptographic keys throughout their entire lifecycle, organizations reduce security risks and improve control over digital assets.
A structured key management approach also supports compliance, improves visibility, and simplifies security operations. As modern systems continue to evolve, investing in proper key management remains a critical step toward building a secure and resilient digital environment.
To see how a centralized Key Management System works in practice, explore a live demo here: